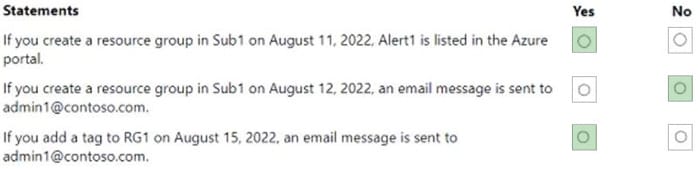
There has never been a time when opportunities and challenges coexisted. The Microsoft AZ-204 exam is the same. To pass the exam, you need to possess the new AZ-204 dumps with practice questions 2024.
Download new AZ-204 dumps 2024 https://www.pass4itsure.com/az-204.html You can choose two ways to pass (PDF or VCE).
In 2024, everything has changed. exam AZ-204: Developing Solutions for Microsoft Azure has also changed.
What should you do in the face of changes to the AZ-204 exam?
Are you ready for the challenges of the Microsoft AZ-204 exam? As the Azure platform and technology are constantly evolving, the specific content and requirements of the exam may change, and the process of earning this certification can sometimes seem overwhelming, filled with countless tasks that require your attention.
However, keep one thing in mind and choose the most up-to-date resources (AZ-204 dumps as well as practice questions 2024), and you will surely be able to complete this process and achieve your goals.
New Microsoft exam AZ-204:
The AZ-204 exam was updated on January 22, 2024. Overall, the changes are minor. A new topic has been added to the new AZ-204 exam called Microsoft Fabric.
For details, you can check out this video (shared by Scott Duffy @ GetCloudSkills), which shows a comparison of the changes between the old and new content of the exam, which is clear at a glance.
The AZ-204 exam needs to be equipped with new learning resources.
So, the new Microsoft AZ-204 exam study resources 2024 are collated for you (Attach a link):
Video:
- Preparing for AZ-204 – Develop Azure compute solutions (1 of 5)
- Preparing for AZ-204 – Develop Azure storage (2 of 5)
- Preparing for AZ-204 – Implement Azure Security (3 of 5)
- Preparing for AZ-204 – Monitor, troubleshoot, and optimize Azure solutions (4 of 5)
- Preparing for AZ-204 – Connect to and consume Azure services and third-party services (5 of 5)
Documentation:
- Preparing for AZ-204 – Develop Azure compute solutions (1 of 5)
- Azure developers, beta exam AZ-204 is just for you
- Exam AZ-204: Developing Solutions for Microsoft Azure – Certifications
- Microsoft Certified: Azure Developer Associate – Certifications
- Preparing for AZ-204 – Develop for Azure storage (segment 2 of 5)
Book:
- Exam Ref AZ-204 Developing Solutions for Microsoft Azure
- Microsoft windows azure development cookbook
- Mastering Cloud Development using Microsoft Azure
Updated in 2024, some AZ-204 dumps practice questions are shared online
| Source: Pass4itSure AZ-204 Dump 2024 | Questions: 15 (495) | Other related Microsoft exams: AZ-104, AZ-305, DP-500 |
Question 1:
You are updating an application that stores data on Azure and uses Azure Cosmos DB for storage. The application stores data in multiple documents associated with a single username.
The application requires the ability to update multiple documents for a username in a single ACID operation.
You need to configure Azure Cosmos DB.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Create a collection based on username to store documents.
B. Configure Azure Cosmos DB to use the Gremlin API.
C. Create an unshared collection to store documents.
D. Configure Azure Cosmos DB to use the MongoDB API.
Correct Answer: CD
Explanation:
C: Multi-document transactions, Requirements
Multi-document transactions are supported within an unshaded collection in API version 4.0. Multi-document transactions are not supported across collections or in shared collections in 4.0.
D: In Azure Cosmos DB for MongoDB, operations on a single document are atomic. Multi-document transactions enable applications to execute atomic operations across multiple documents. It offers “all-or-nothing” semantics to the
operations. On commit, the changes made inside the transactions are persisted and if the transaction fails, all changes inside the transaction are discarded.
Multi-document transactions follow ACID semantics:
Atomicity: All operations are treated as one Consistency: Data committed is valid Isolation: Isolated from other operations Durability: Transaction data is persisted when the client is told so
Reference: https://learn.microsoft.com/en-us/azure/cosmos-db/mongodb/use-multi-document-transactions
Question 2:
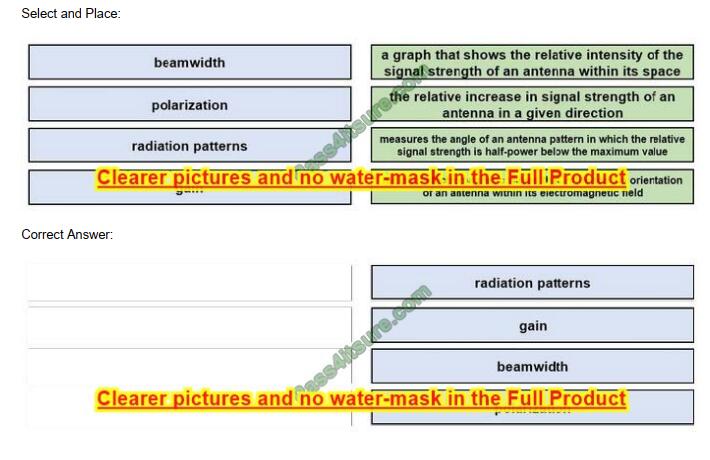
HOTSPOT
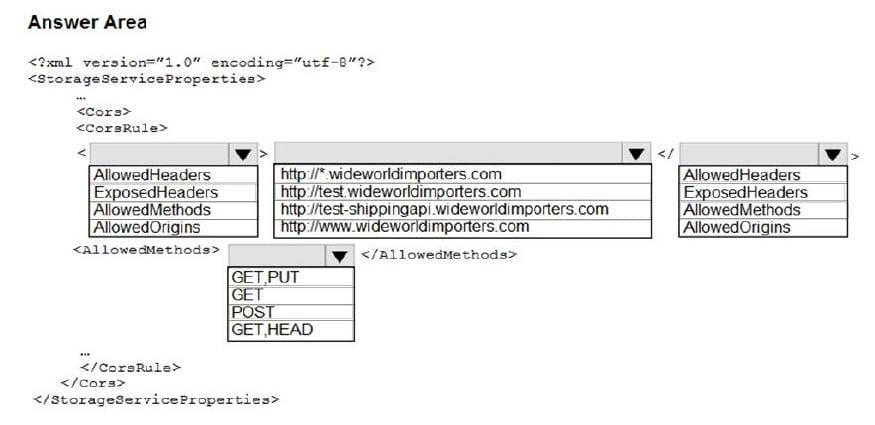
How should you configure the Azure Table Storage service? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
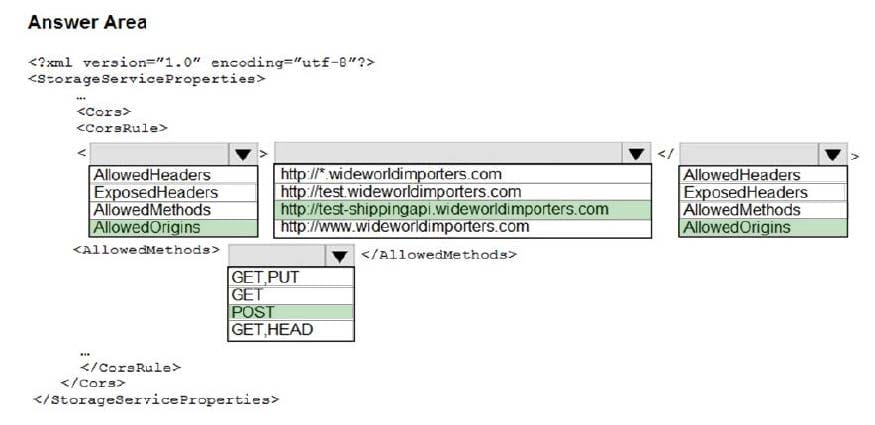
Box 1: AllowedOrigins
A CORS request will fail if Access-Control-Allow-Origin is missing.
Scenario:

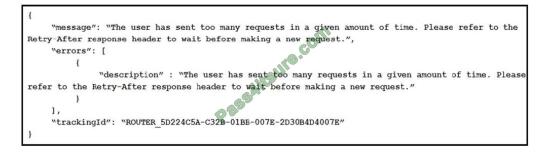
The following error message displays while you are testing the website:
Box 2: http://test-shippingapi.wideworldimporters.com
Syntax: Access-Control-Allow-Origin: *
Access-Control-Allow-Origin:
Access-Control-Allow-Origin: null
Specifies an origin. Only a single origin can be specified.
Box 3: AllowedOrigins
Box 4: POST
The only allowed methods are GET, HEAD, and POST. In this case, POST is used.
“allowed methods” Failed to load no “Access-control-Origin” header is present
References:
https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Access-Control-Allow-Origin
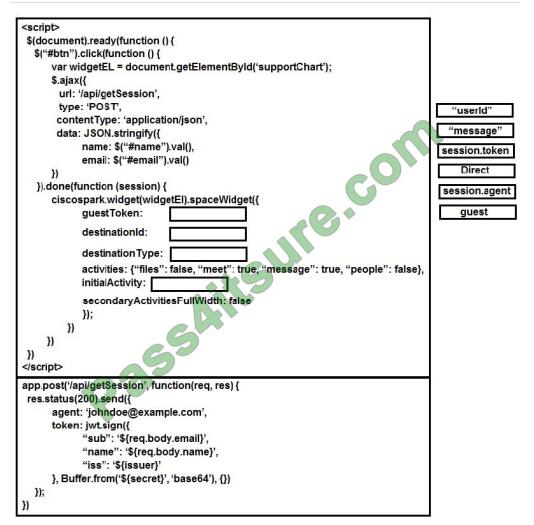
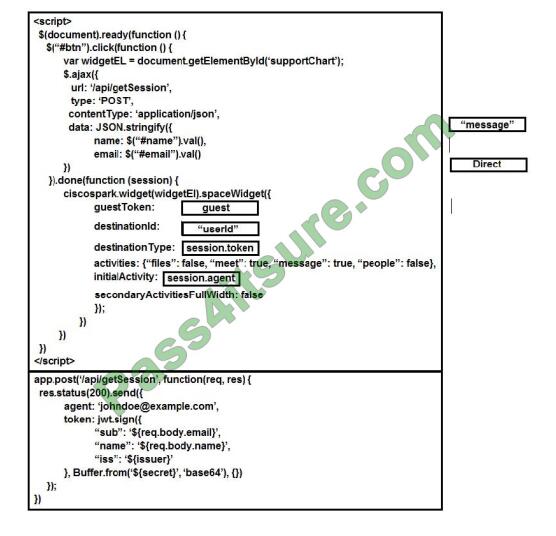
Question 3:
HOTSPOT
You are creating an app that uses Event Grid to connect with other services. Your app\’s event data will be sent to a serverless function that checks compliance. This function is maintained by your company.
You write a new event subscription at the scope of your resource. The event must be invalidated after 3 specific period of time. You need to configure the Event Grid to ensure security.
What should you implement? To answer, select the appropriate options in the answer area;
NOTE: Each correct selection is worth one point
Hot Area:
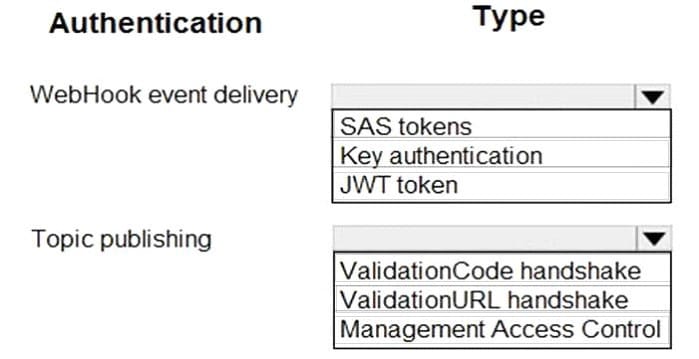
Correct Answer:
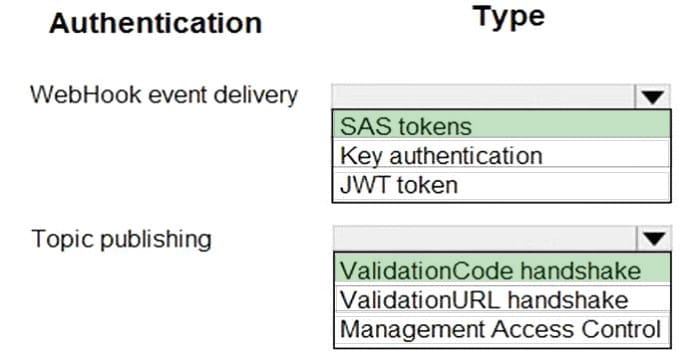
Box 1: SAS tokens
Custom topics use either Shared Access Signature (SAS) or key authentication.
Microsoft recommends SAS, but key authentication provides simple programming and is compatible with many existing webhook publishers.
In this case, we need the expiration time provided by SAS tokens.
Box 2: ValidationCode handshake
Event Grid supports two ways of validating the subscription: ValidationCode handshake (programmatic) and ValidationURL handshake (manual).
If you control the source code for your endpoint, this method is recommended.
Incorrect Answers:
ValidationURL handshake (manual): In certain cases, you can’t access the source code of the endpoint to implement the ValidationCode handshake. For example, if you use a third-party service (like Zapier or IFTTT), you can\’t
programmatically respond with the validation code.
References:
https://docs.microsoft.com/en-us/azure/event-grid/security-authentication
Question 4:
You are developing an Azure-based web application. The application goes offline periodically to perform offline data processing. While the application is offline, numerous Azure Monitor alerts fire which results in the on-call developer being paged. The application must always log in when the application is offline for any reason.
You need to ensure that the on-call developer is not paged during offline processing.
What should you do?
A. Add Azure Monitor alert processing rules to suppress notifications.
B. Create an Azure Monitor Metric Alert.
C. Build an Azure Monitor action group that suppresses the alerts.
D. Disable Azure Monitor Service Health Alerts during offline processing.
Correct Answer: C
You can use alert processing rules to add action groups or remove (suppress) action groups from your fired alerts. Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/alerts/alerts-action-rules
Question 5:
You are implementing an Azure API app that uses built-in authentication and authorization functionality.
All app actions must be associated with information about the current user.
You need to retrieve the information about the current user.
What are two ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. HTTP headers
B. environment variables
C. /.auth/me HTTP endpoint
D. /.auth/login endpoint
Correct Answer: AC
A: After App Service Authentication has been configured, users trying to access your API are prompted to sign in with their organizational account that belongs to the same Azure AD as the Azure AD application used to secure the API. After signing in, you can access the information about the current user through the HttpContext.Current.User property.
C: While the server code has access to request headers, the client code can access GET /.auth/me to get the same access tokens (
References: https://docs.microsoft.com/en-us/azure/app-service/app-service-web-tutorial-auth-aad https://docs.microsoft.com/en-us/sharepoint/dev/spfx/web-parts/guidance/connect-to-api-secured-with-aad
Question 6:
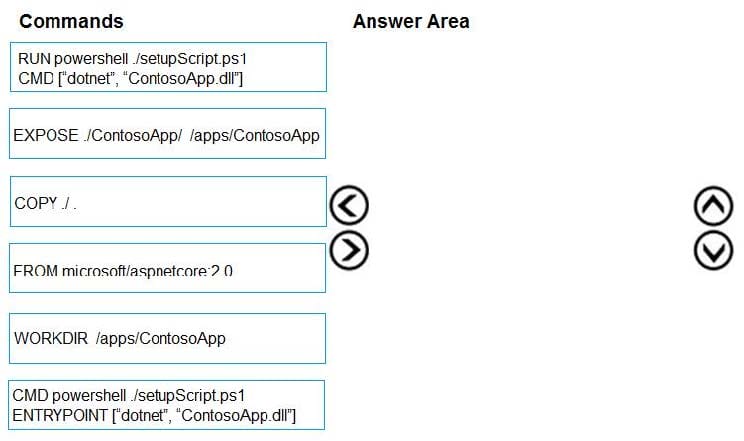
DRAG DROP
You plan to create a Docker image that runs as an ASP.NET Core application named ContosoApp. You have a setup script named setupScript.ps1 and a series of application files including ContosoApp.dll.
You need to create a Dockerfile document that meets the following requirements:
1. Call setup script.ps1 when the container is built.
2. Run ContosoApp.dll when the container starts.
The Docker document must be created in the same folder where ContosoApp.dll and setupScript.ps1 are stored.
Which four commands should you use to develop the solution? To answer, move the appropriate commands from the list of commands to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
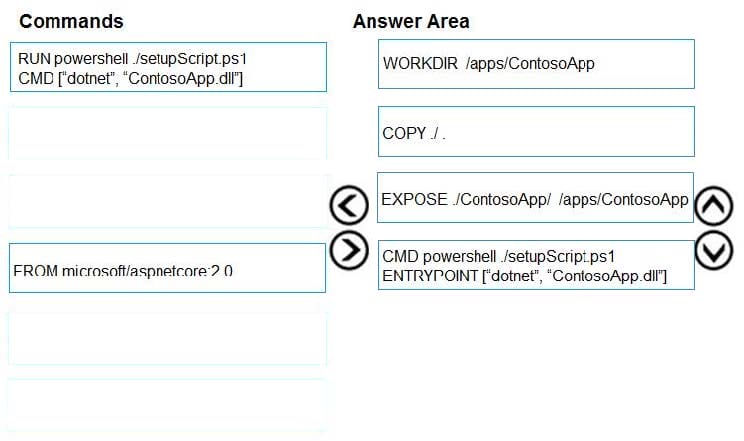
Step 1: WORKDIR /apps/ContosoApp
Step 2: COPY ./The Docker document must be created in the same folder where ContosoApp.dll and setup script.ps1 are stored.
Step 3: EXPOSE ./ContosApp/ /app/ContosoApp
Step 4: CMD powershell ./setupScript.ps1
ENTRYPOINT [“dotnet”, “ContosoApp.dll”]
You need to create a Dockerfile document that meets the following requirements:
Call setup script.ps1 when the container is built.
Run ContosoApp.dll when the container starts.
References:
https://docs.microsoft.com/en-us/azure/app-service/containers/tutorial-custom-docker-image
Question 7:
HOTSPOT
You plan to deploy a new application to a Linux virtual machine (VM) that is hosted in Azure.
The entire VM must be secured at rest by using industry-standard encryption technology to address organizational security and compliance requirements.
You need to configure Azure Disk Encryption for the VM.
How should you complete the Azure CLI commands? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
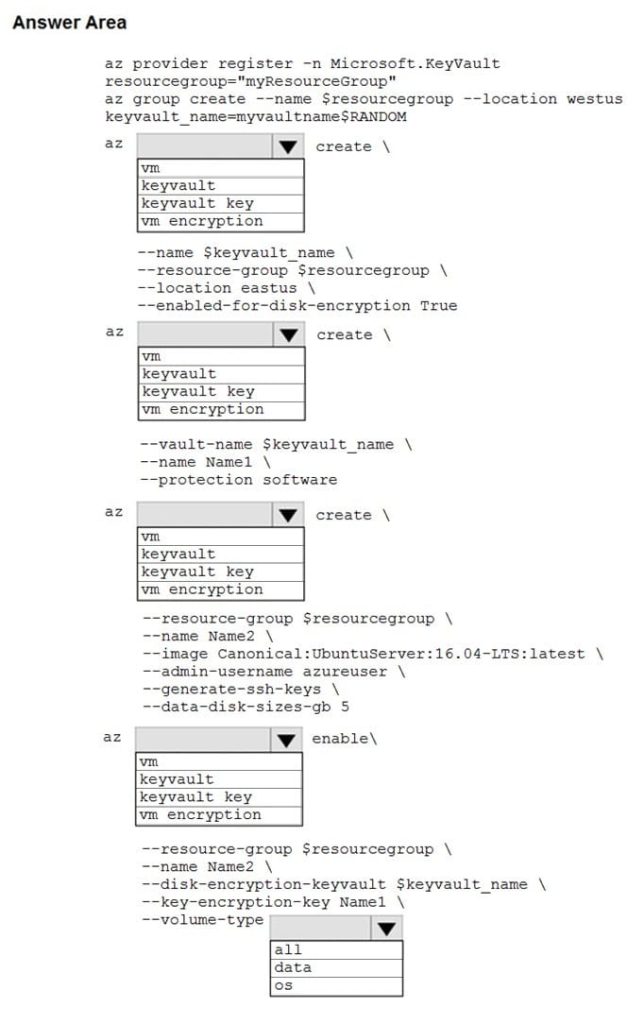
Correct Answer:
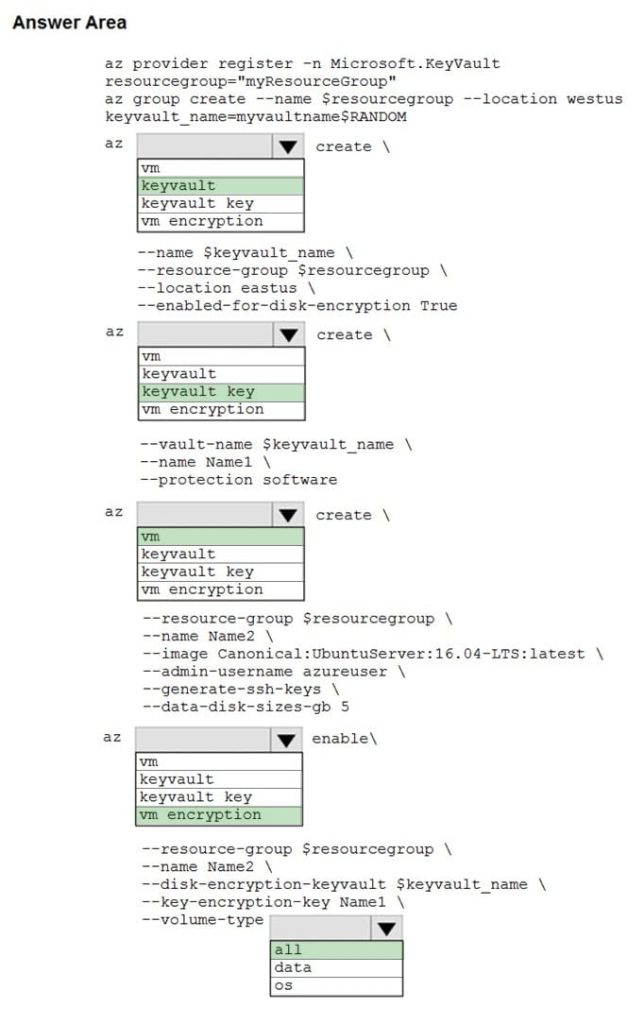
Box 1: key vault
Create an Azure Key Vault with az key vault and enable the Key Vault for use with disk encryption. Specify a unique Key Vault name for keyvault_name as follows:
keyvault_name=myvaultname$RANDOM
az key vault create \ –name $keyvault_name \ –resource-group $resourcegroup \ –location east us \ –enabled-for-disk-encryption True
Box 2: key vault key The Azure platform needs to be granted access to request the cryptographic keys when the VM boots to decrypt the virtual disks. Create a cryptographic key in your Key Vault with az key vault key create. The following example creates a key named myKey:
az key vault key create \ –vault-name $keyvault_name \ –name myKey \ –protection software
Box 3: vm
Create a VM with az vm create. Only certain marketplace images support disk encryption. The following example creates a VM named myVM using an Ubuntu 16.04 LTS image:
az vm create \ –resource-group $resourcegroup \ –name my VM \ –image Canonical:UbuntuServer:16.04-LTS:latest \ –admin-username azure user \ –generate-ssh-keys \
Box 4: vm encryption
Encrypt your VM with az vm encryption enable:
az vm encryption enable \ –resource-group $resourcegroup \ –name my VM \ –disk-encryption-key vault $keyvault_name \ –key-encryption-key myKey \ –volume-type all
Note: There seems to be an error in the question. Should have enabled it instead of creating it.
Box 5: all
Encrypt both data and operating system.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/linux/disk-encryption-cli-quickstart
Question 8:
A company is developing a solution that allows smart refrigerators to send temperature information to a central location. You have an existing Service Bus.
The solution must receive and store messages until they can be processed. You create an Azure Service Bus instance by providing a name, pricing tier, subscription, resource group, and location.
You need to complete the configuration.
Which Azure CLI or PowerShell command should you run?
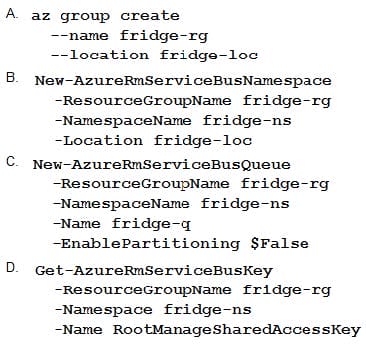
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: C
A service bus instance has already been created (Step 2 below). Next is step 3, Create a Service Bus queue.
Note:
Steps:
Step 1: # Create a resource group
resourceGroupName=”myResourceGroup”
az group create –name $resourceGroupName –location east
Step 2: # Create a Service Bus messaging namespace with a unique name
namespaceName=myNameSpace$RANDOM
az service bus namespace create –resource-group $resourceGroupName –name $namespaceName –location east
Step 3: # Create a Service Bus queue
az service bus queue create –resource-group $resourceGroupName –namespace-name $namespaceName –name BasicQueue
Step 4: # Get the connection string for the namespace
connectionString=$(az service bus namespace authorization-rule keys list –resource-group $resourceGroupName –namespace-name $namespaceName –name RootManageSharedAccessKey –query primaryConnectionString –output tsv)
Reference:
https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-quickstart-cli
Question 9:
You are developing a complex workflow by using Azure Durable Functions.
During testing, you observe that the results of the workflow differ based on how many instances of the Azure Function are running.
You need to resolve the issue.
What should you do?
A. Ensure that all Orchestrator code is deterministic.
B. Read all state data from the durable function context
C. Configure the Azure Our able function to run on an App Service Plan with one instance.
D. Implement the monitor pattern within the workflow.
Correct Answer: A
Question 10:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
You are developing and deploying several ASP.Net web applications to Azure App Service.
You plan to save session state information and HTML output.
You must use a storage mechanism with the following requirements:
1.Share session state across all ASP.NET web applications
2.Support controlled, concurrent access to the same session state data for multiple readers and a single writer
3.Save full HTTP responses for concurrent requests
You need to store the information.
Proposed Solution: Add the web applications to Docker containers. Deploy the containers. Deploy the containers to Azure Kubernetes Service (AKS).
Does the solution meet the goal?
A. Yes
B. No
Correct Answer: B
Instead, use Azure Cache for Redis.
Note: Azure Cache for Redis provides a session state provider that you can use to store your session state in memory with Azure Cache for Redis instead of a SQL Server database. To use the caching session state provider, first, configure your cache, and then configure your ASP.NET application for the cache using the Azure Cache for Redis Session State NuGet package.
References: https://docs.microsoft.com/en-us/azure/azure-cache-for-redis/cache-aspnet-session-state-provider
Question 11:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You develop and deploy an Azure App Service API app to a Windows-hosted deployment slot named Development. You create additional deployment slots named Testing and Production. You enable auto swap on the Production
deployment slot.
You need to ensure that scripts run and resources are available before a swap operation occurs.
Solution: Enable auto swap for the Testing slot. Deploy the app to the Testing slot.
Does the solution meet the goal?
A. No
B. Yes
Correct Answer: B
Instead, update the web. config file to include the application initialization configuration element. Specify custom initialization actions to run the scripts.
Note: Some apps might require custom warm-up actions before the swap. The application initialization configuration element in web. config lets you specify custom initialization actions. The swap operation waits for this custom warm-up to finish before swapping with the target slot. Here \ is a sample web. config fragment.
Reference: https://docs.microsoft.com/en-us/azure/app-service/deploy-staging-slots#troubleshoot-swaps
Question 12:
DRAG DROP
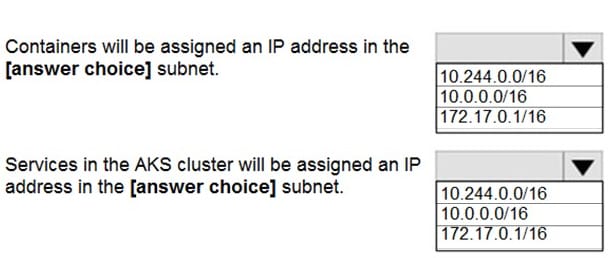
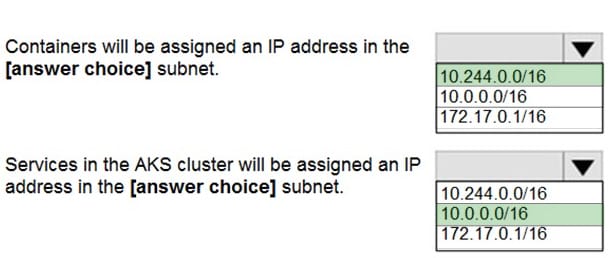
You are preparing to deploy an application to an Azure Kubernetes Service (AKS) cluster.
The application must only be available from within the VNet that includes the cluster.
You need to deploy the application.
How should you complete the deployment of YAML? To answer, drag the appropriate YAML segments to the correct locations. Each YAML segment may be used once, more than once, or not at all. You may need to drag the split bar between
panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
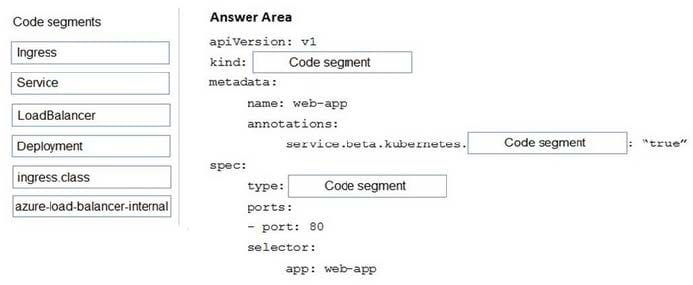
Correct Answer:
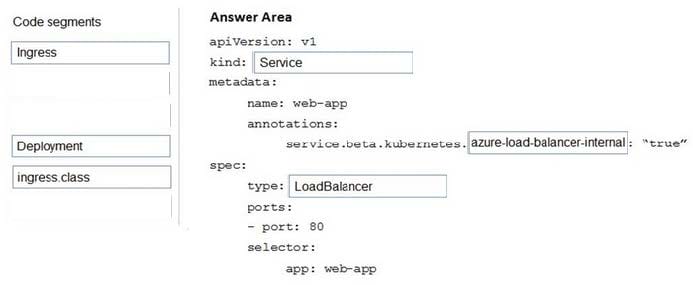
To create an internal load balancer, create a service manifest named internal-lb.yaml with the service type LoadBalancer and the azure-load-balancer-internal annotation as shown in the following example:
YAML:
apiVersion: v1
kind: Service
metadata:
name: internal-app
annotations:
service.beta.kubernetes.io/azure-load-balancer-internal: “true” spec:
type: LoadBalancer
ports:
-port: 80 selector: app: internal-app
References: https://docs.microsoft.com/en-us/azure/aks/internal-lb
Question 13:
You are a developer at your company.
You need to update the definitions for an existing Logic App.
What should you use?
A. the Enterprise Integration Pack (EIP)
B. the Logic App Code View
C. the API Connections
D. the Logic Apps Designer
Correct Answer: B
Edit JSON – Azure portal
Sign in to the Azure portal.
From the left menu, choose All Services. In the search box, find “logic apps”, and then from the results, select your logic app.
On your logic app\’s menu, under Development Tools, select Logic App Code View. The Code View editor opens and shows your logic app definition in JSON format.
Reference:
https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-enterprise-integration-overview
https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-author-definitions
Question 14:
HOTSPOT
You are developing an Azure App Service hosted ASP.NET Core web app to deliver video-on-demand streaming media. You enable an Azure Content Delivery Network (CDN) Standard for the web endpoint. Customer videos are downloaded
from the web app by using the following example URL.: http://www.contoso.com/content.mp4?quality=1
All media content must expire from the cache after one hour. Customer videos with varying quality must be delivered to the closest regional point of presence (POP) node.
You need to configure Azure CDN caching rules.
Which options should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
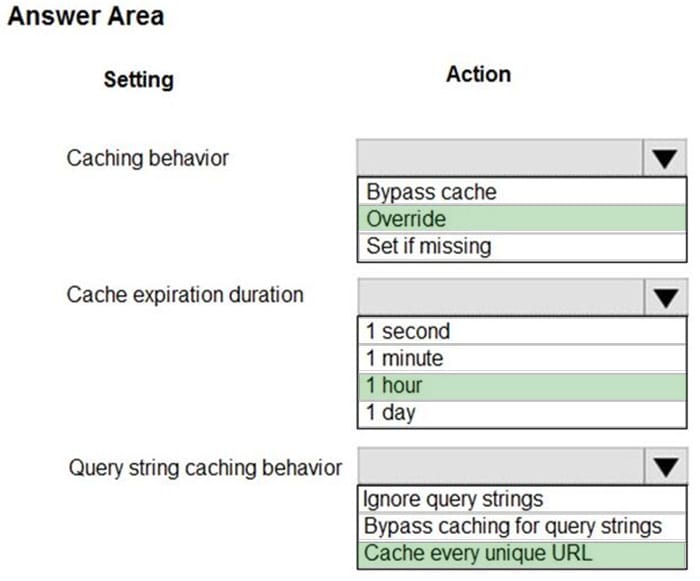
Box 1: Override
Override: Ignore the origin-provided cache duration; use the provided cache duration instead. This will not override cache-control: no-cache.
Set if missing: Honor origin-provided cache-directive headers, if they exist; otherwise, use the provided cache duration.
Incorrect:
Bypass cache: Do not cache and ignore origin-provided cache-directive headers.
Box 2: 1 hour
All media content must expire from the cache after one hour.
Box 3: Cache every unique URL
Cache every unique URL: In this mode, each request with a unique URL, including the query string, is treated as a unique asset with its cache. For example, the response from the origin server for a request for example.ashx?q=test1 is
cached at the POP node and returned for subsequent caches with the same query string. A request for example.ashx?q=test2 is cached as a separate asset with its time-to-live setting.
Incorrect Answers:
Bypass caching for query strings: In this mode, requests with query strings are not cached at the CDN POP node. The POP node retrieves the asset directly from the origin server and passes it to the requestor with each request.
Ignore query strings: Default mode. In this mode, the CDN point-of-presence (POP) node passes the query strings from the requestor to the origin server on the first request and caches the asset. All subsequent requests for the asset that are
served from the POP ignore the query strings until the cached asset expires.
Reference:
https://docs.microsoft.com/en-us/azure/cdn/cdn-query-string
Question 15:
DRAG DROP
You develop and deploy an Azure App Service web app. The web app accesses data in an Azure SQL database.
You must update the web app to store frequently used data in a new Azure Cache for the Redis Premium instance.
You need to implement the Azure Cache for Redis features.
Which feature should you implement? To answer, drag the appropriate feature to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view
content.
NOTE: Each correct selection is worth one point.
Select and Place:
Correct Answer:
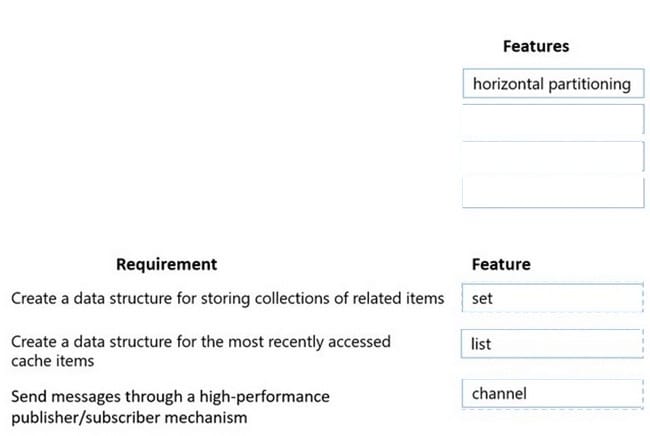
Reference: https://www.red-gate.com/simple-talk/development/dotnet-development/overview-of-azure-cache-for-redis/ https://docs.microsoft.com/en-us/azure/architecture/best-practices/caching
More Microsoft exam questions. . .
Questions you want to ask: AZ-204 exam
Is there any change in difficulty after the AZ-204 exam 2024 update?
I don’t think so, passing the AZ-204 exam is still the same level of difficulty as before, you need a new AZ-204 dumps, you need a new AZ-204 practice, you need to prepare carefully.
Treat the new AZ-204 exam, do I still need to prepare?
Yes, just like any exam or certification, preparation is crucial. Preparation means planning, understanding exam details, dedicating spare time to study and study.
Where should the AZ-204 exam be focused?
I think the focus is: how do you as a software engineer or a cloud engineer solve any cloud-related use case scenarios. This is the point.
The new AZ-204 dumps 2024 and the new AZ-204 practice questions 2024 are the ones that will really help you to prepare for the exam easily and get certified.
What you need to do is: Download the newly updated AZ-204 practice questions 2024 inside the AZ-204 dumps 2024 https://www.pass4itsure.com/az-204.html (PDF or VCE) exercises, prepare diligently, and win the exam.